Human Resource Management System
New Time Approvals by Employee Section in Time and Labor WorkCenter
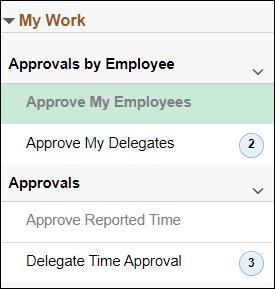
In response to customer feedback, ITS will be implementing a new section in the Time and Labor WorkCenter titled Approvals by Employee on February 8, 2023. This time approval flow groups approvals by employee AND takes you to the earliest time period that needs approval. This is similar to the time approval method before the February 2022 upgrade.
The new “Approvals by Employee” section displays only your employees who have time that needs approval (no need to use filters). Selecting the employee launches the Enter Time page for the earliest time period that needs approval, where you can approve the entire pay period at once.
Safe Computing
Article: February Privacy Event
Data Privacy Day (Data Protection Day in the EU) is January 28th! To celebrate at U-M, ITS Information Assurance (IA) is hosting privacy events throughout February. These sessions are intended to raise awareness, promote best practices, and provoke thought and conversation on privacy topics broadly relevant to our community members and society at large.
- February 8, 2023, at noon - Child Safety in the Smart Home: Our presenter, Kaiwen Sun, is a Ph.D. student at the University of Michigan whose research focuses on the intersection of children’s privacy and safety and understanding parents’ perceptions and behaviors around privacy and safety in the context of smart home technologies. This event is open to the U-M community (umich login required) and will be especially relevant to parents, grandparents, guardians, and others who interact with children in their homes. This event will not be recorded.
- February 17, 2023, at 11 AM - Privacy Keynote on Technology, AI, and Ethics: Register to join the 2023 Privacy@Michigan keynote with Dr. Kirsten Martin. Dr. Martin is the Director of the Notre Dame Technology Ethics Center and the William P. and Hazel B. White Professor of Technology Ethics and Professor of IT, Analytics, and Operations in the Mendoza College of Business at the University of Notre Dame, where she hosts the podcast TEC Talks. Dr. Martin is a University of Michigan College of Engineering alumna and we are thrilled to welcome her back on the Ann Arbor campus. This event will be hosted in-person, live-streamed, and recorded.
Refer to the Privacy@Michigan event page for more details and to register for the Privacy@Michigan keynote. Be sure to check the Safe Computing calendar for cybersecurity and privacy events throughout the year.
Safe Computing: In the News
U-M ITS Safe Computing: In the News is your source for the latest headlines on information security and privacy. At the start of the new year, media outlets are highlighting the increased persistence and sophistication of scammers, and are offering tips on protecting yourself.
CNBC’s article on the increase of phishing attacks cites a recent study by SlashNext that found a 61% increase in the rate of phishing attacks from URLs, attachments, and messaging in email, mobile and browser channels, with a 50% increase in phishing attacks coming through mobile devices. In an article about scam calls targeting older adults, The Wall Street Journal shares a Federal Trade Commission’s finding that 24% of adults in the US over age 50 lost money to a phone call scam in 2021.
As attacks increase in frequency and savvy, it’s important to continue learning how to protect yourself. Here are some tips from these articles:
- Be vigilant about checking sources when giving your personal information. If you receive an unexpected email asking for urgent information or financial details, do not open attachments or click on unfamiliar links. Instead, reach out to the person or organization to confirm the communication is legitimate.
- Use anti-phishing software and other cyber security tools to protect your personal and work data. Tools such as Multi-factor authentication can ensure no one but you is accessing your accounts.
- Use virtual assistants, call blocking, and robocall apps to avoid unknown callers.
- Ignore unknown emails, texts, and calls. Instead, contact the business through a separate channel, such as their website, to ask about the related message.
As always, being aware of the latest scams and phishing techniques and following tips for avoiding them is the best defense for you, your data, and the U. Find more cybersecurity and privacy news and resources on Safe Computing.
Article: Online Harassment
Having a presence on the internet in any form means there’s a real possibility you've faced online harassment or witnessed someone become a victim of it. A Pew Research Center survey found that 41% of Americans have experienced some form of this type of harassment, which is defined as the “pervasive or severe targeting of an individual or group online through harmful behavior.” This harmful behavior can be confusing, frightening, and, in some cases, have dangerous consequences.
Online harassment can occur while using everyday digital technologies such as social media, gaming platforms, and email applications. Many people have reported doubt and confusion over these tactics and are often unsure whether they are being harassed. Need help recognizing online harassment? The following are the seven most common types of online harassment:
- Cyberstalking: Organized and repeated threats or intimidation.
- Impersonation: Using the name or persona of someone else without their consent and with the intent to harm, intimidate, defraud, or threaten another individual.
- Catfishing: Creation of a fictitious identity for the purpose of starting a relationship with someone online. Though this behavior is not illegal, it is unethical and can be dangerous.
- Trolling: Producing controversial, unsolicited comments online that are made specifically to provoke individuals and elicit an emotional response.
- Doxxing: Publication of someone’s personal information that could include anything from home address, phone number, or information about family members with the express intent of others harassing them.
- Swatting: Action of making a prank call to emergency services in an attempt to bring a large number of armed police officers to that individual’s address.
- Sexual harassment: the online form of sexual harassment refers to the act of distributing private, explicit images or videos online without the permission of the person in the images/videos.
It is not hard to imagine how online harassment has affected so many individuals or wonder why it is so widespread. With an abundance of polarizing topics being discussed in our society, there are many reasons for the proliferation of online hate. It’s important to identify, document, and report incidents of harassment, along with blocking any online identities that perpetuate harassment. Most social media and online messaging platforms have created avenues for reporting and removing offensive content.
Remember, this abuse is never your fault and you are not without the power to fight back and protect yourself. Often, a good place to start is to increase your online security through using complex and unique passwords, enabling two-factor authentication, and protecting your messages with encrypted apps.
Here are additional resources to assist you in preventing and responding to online harassment:
U-M Resources:
- Report a crime or concern to DPSS
- Access the U-M Harassment and Discrimination Reporting Form
- Refer to U-Ms Sexual and Gender-based Misconduct and Reporting Resources
- Refer to Safe Computing’s Protect Your Privacy